Datadog Application Performance Monitoring (APM)
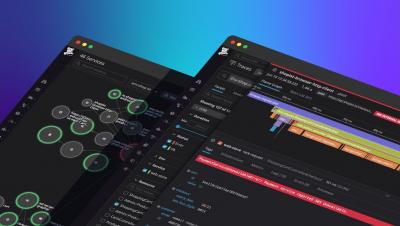
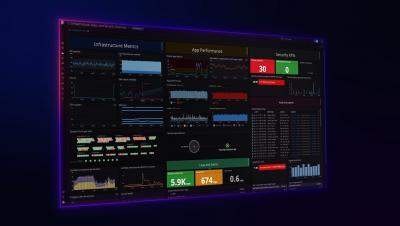
Datadog APM provides end-to-end application monitoring, from frontend browsers to backend database queries and code profiles, so you can monitor and optimize your stack at any scale—no sampling required. APM and distributed tracing are fully integrated with the rest of Datadog, giving you rich context for troubleshooting issues in real time.