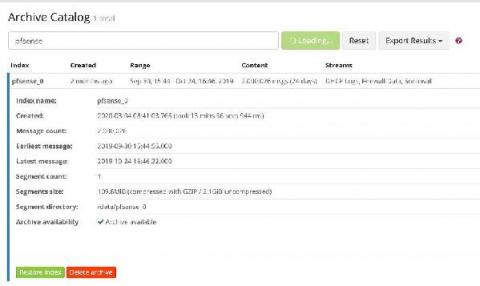
How Does Archiving Work in Graylog?
Every week we get many great questions through support, the community, social media, and our weekly demo. On Fridays, I like to share the most common questions and answers, tips, insights, a closer look at Graylog, interviews, etc. If you have any questions for me, drop them on Twitter, and I’ll do my best to fold them into upcoming Friday posts. Our handle is @graylog2.