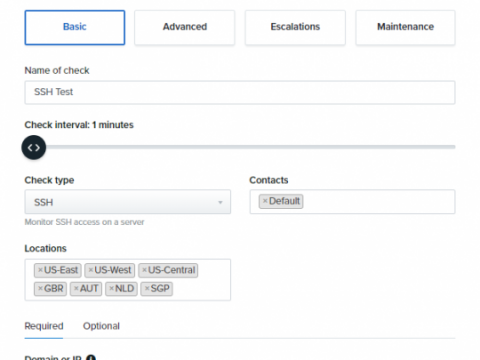
Introducing Uptime.com's New UI
We want to begin this post by thanking our long-time Uptime.com members for bearing with us through the transition to our new user interface. You have no doubt noticed the changes. The adjustments to the UI are small, but some important features are now in a different place. Our intent was a more intuitive design. Today, we’ll walk you through some of our most important decisions in this post. First, we’ll document some changes to be aware of.