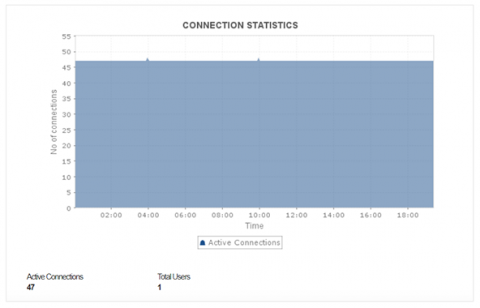
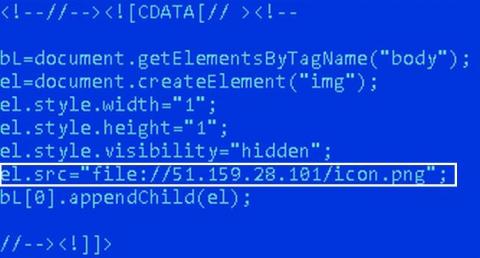
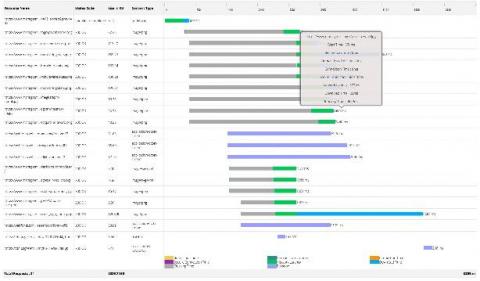
Key metrics for PostgreSQL performance monitoring
PostgreSQL offers flexibility on how data is stored and compared in a relational database. This is why it’s so popular among enterprises as a solution for their database requirements. Although PostgreSQL is quite reliable, database problems are inevitable, especially in large-scale environments. Ignoring these problems could result in a plunge in the productivity of your business.