Operations | Monitoring | ITSM | DevOps | Cloud
September 2020
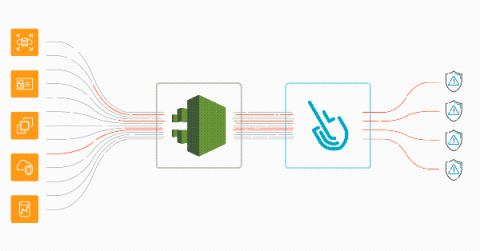
AWS threat detection using CloudTrail and Sysdig Secure
Implementing AWS threat detection with Sysdig Secure takes just a few minutes. Discover how to improve the security of your cloud infrastructure using AWS CloudTrail and Sysdig Cloud Connector. With the rise of microservices and DevOps practices, a new level of dangerous actors threatens the cloud environment that governs all of your infrastructure. A malicious or inattentive cloud API request could have a sizable impact on availability, performance, and last but not least, billing.
Securing and Monitoring AWS Container Services
Fargate scanning in under 4 minutes
Automate Fargate image scanning
Discover how to automate AWS Fargate image scanning directly in your AWS environment and block vulnerabilities from reaching production, among other threats. AWS Fargate and ECS allow you to deploy containerized workloads quickly. Fargate is even more convenient, as you don’t have to take care of the infrastructure.
How to monitor Istio, the Kubernetes service mesh
In this article, we are going to deploy and monitor Istio over a Kubernetes cluster. Istio is a service mesh platform that offers advanced routing, balancing, security, and high availability features, plus Prometheus-style metrics for your services out-of-the-box.
Five Prometheus exporters best practices to increase your productivity
The following Prometheus exporters best practices will help you implement a monitoring solution based on Prometheus, and will also increase your productivity. Prometheus is one of the foundations of the cloud-native environment. It has become the de-facto standard for visibility in Kubernetes environments, creating a new category called Prometheus monitoring.
What's new in Sysdig - September 2020
Welcome to our monthly update on what’s new from Sysdig! This month is a little eclipsed by last month’s big launch of Essentials and our new SaaS regions, KubeCon EU, and many of us finishing off the summer holidays and getting the kids packed off back to school. Our teams are busy working on some big feature releases which we don’t want to reveal just yet, but I think you’re all going to really love them in the coming months!
Manage AppArmor profiles in Kubernetes with kube-apparmor-manager
Discover how Kube-apparmor-manager can help you manage AppArmor profiles on Kubernetes to reduce the attack surface of your cluster. AppArmor is a Linux kernel security module that supplements the standard Linux user and group-based permissions to confine programs to a limited set of resources. AppArmor can be configured for any application to reduce its potential attack surface and provide greater in-depth defense.
Detecting CVE-2020-14386 with Falco and mitigating potential container escapes
On September 14, CVE-2020-14386 was reported as a “high” severity threat. This CVE is a kernel security vulnerability that enables an unprivileged local process to gain root access to the system. CVE-2020-14386 is a result of a bug found in the packet socket facility in the Linux kernel. It allows a bad actor to trigger a memory corruption that can be exploited to hijack data and resources and in the most severe case, completely take over the system.
Secure and monitor AWS Outposts and hybrid clouds
Today we announced that Sysdig has demonstrated successful integration of our monitoring and security software with AWS Outposts and achieved the AWS Outposts Ready designation. AWS Outposts provides a fully managed service that extends AWS infrastructure, services, APIs, and tools to your datacenter, co-location space or “edge” location to support on-prem and hybrid cloud use cases. AWS Outposts provides a hardware and software stack built on Amazon’s EC2 public cloud expertise.
Seven Kubernetes monitoring best practices every monitoring solution should enable
Look out for these Kubernetes monitoring best practices when evaluating a Kubernetes monitoring solution. It will be easier to make sense of them if your tools are Kubernetes native. Let’s face it. Running containers in Kubernetes brings a number of advantages in terms of automation, segmentation, and efficiency. However, the ability to monitor performance and availability in an ever-changing infrastructure like Kubernetes can be a challenge.
Containers and Kubernetes may be the edge you need to keep moving forward
If it wasn’t clear before the global pandemic, it is now: Cloud applications can keep businesses moving forward. During this time, people have been able to shop, connect with friends and, of course, work from home.
Sysdig Secure DevOps Platform available on Red Hat Marketplace
Sysdig is pleased to announce that the Sysdig Secure DevOps Platform is now available through Red Hat Marketplace.