Operations | Monitoring | ITSM | DevOps | Cloud
June 2021
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent need to scrutinize and control the use of these online resources to prevent data theft, exposure, and loss. This blog elaborates on how a robust URL filtering solution can help manage what cloud services your employees use and how they interact with these services.
Five worthy reads: Internet of Behaviors - Exploring beyond the Internet of Things
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week let’s welcome a new acronym to the club — IoB (Internet of Behaviors) and assess its impact. Organizations are making the best use of analytics, A/B testing, and more amazing things to map the perfect customer journey. Here comes the missing piece to building an ideal user journey: Internet of Behavior (IoB).
Unified agent for asset discovery for ServiceDesk Plus
Fine-tune network uptime monitoring with OpManager
Uptime monitoring has a direct impact on your organization’s ability to support end-users and deliver services. Not maintaining adequate uptime can interfere with business productivity and impact end-user satisfaction, eventually resulting in financial losses. Establishing uptime can be a challenging task since there are numerous factors that can act against it.
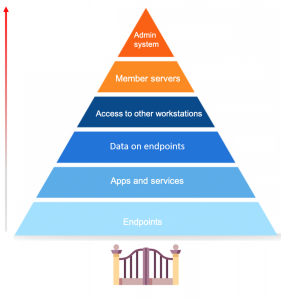
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are end-user devices like desktops, laptops, and mobile devices. They serve as points of access to an enterprise network and create points of entry that function as gateways for malicious actors. Since end-user workstations make up a huge portion of endpoints, we’ll be focusing on their security.
OpManager makes network monitoring easy for Heritage Credit Union
About Heritage Credit Union Heritage Credit Union Limited is a US-based, non-profit financial institution founded in 1934. Today, it serves more than 28,000 members in Illinois and Wisconsin, with $450 million in assets and more than 120 employees. It takes care of its customers’ credit cards, banking, auto loans, mortgages, and savings accounts.
The Colonial Pipeline ransomware attack: Lessons for cybersecurity teams
The recent ransomware attack on Colonial Pipeline is reportedly one of the most significant cyberattacks on the energy sector till date, and it has overwhelmed cybersecurity experts across the globe.
Top 5 causes of network packet loss and how to resolve them with OpManager
Network packets contain pieces of information that are sent and received enabling communication. When these network packets fail to reach their destination, it results in network packet loss. Network packet loss causes heavy latency and disruption, so, when a network suffers packet loss, it can lead to undesirable circumstances, and organizations might even end up losing business.
Five worthy reads: Confidential computing - The way forward in cloud security
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. In light of rising concerns over cloud cybersecurity, this week we explore the concept of confidential computing. The past year has seen strong adoption of cloud technologies due to accelerated digital transformation and a cloud-first approach in business.
5 key challenges in CPU temperature monitoring and how to overcome them
Fluctuations in CPU temperature contribute to a considerable amount of network downtime and lead to network performance deterioration. When the CPU gets overheated, network devices slow down or even shut off; it also affects the performance of other network devices and causes an unpleasant user experience. CPU over utilization is not only a problem in itself but is also an indication of several other issues.
Monitor Azure using Applications Manager
Microsoft Azure is the fastest growing cloud platform at the moment. Many organizations use Microsoft Azure to quickly build and deliver cloud services that can scale or to migrate existing workloads to the cloud. However, larger and faster cloud services can quickly increase the complexity of a network. To solve this and ensure business-critical workloads run correctly, IT teams need deep visibility into their Azure environments.
Multi-client network troubleshooting is now hassle-free with ServiceDesk Plus MSP integration
Managed service providers (MSPs) typically might run into a variety of network issues in a client’s network, and they address them without compromising the performance of other client networks. This requires visibility into multi-client networks, and good sense in decision-making. When it comes to multi-client network monitoring and management, proactively troubleshooting network issues may seem trivial, but they are not.
Resolve network security issues efficiently with the Firewall Analyzer-ServiceDesk Plus integration
ManageEngine Firewall Analyzer reviews firewall logs to capture network security threats. It generates alerts upon detecting security threats and attacks, and notifies you, the security administrator, in real time. You can configure alerts to be sent via email, SMS, and more. With these real-time notifications, you can troubleshoot to take instant remedial action. You can also make changes to your firewall policies and configurations to prevent recurring security incidents.
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.