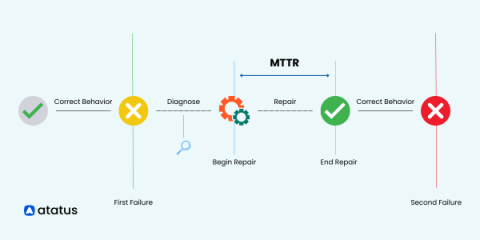
MTTR vs. MTBF vs. MTTF: Understanding Failure Metrics
In the dynamic landscape of software and web applications, failures can have severe consequences, impacting user experience, business continuity, and overall performance. To proactively address these challenges, organizations rely on robust monitoring practices supported by failure metrics. Failure metrics, specifically tailored to software and web application monitoring, provide crucial insights into system health, reliability, and optimization opportunities.