Operations | Monitoring | ITSM | DevOps | Cloud
Sumo Logic
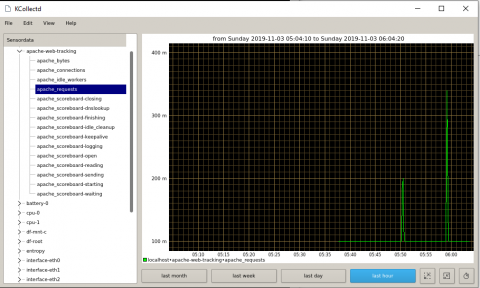
Tracking Systems Metrics with collectd
Understanding the Apache Access Log: View, Locate and Analyze
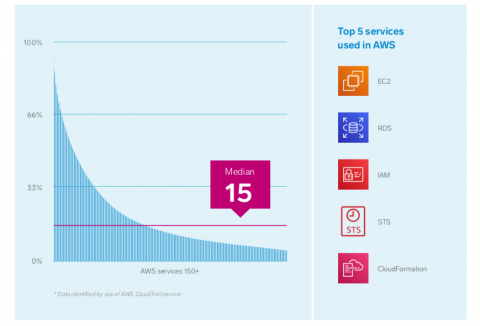
AWS offers 175 services now. Should you be adopting many of them now?
Can You Tell Debug Data and BI Data Apart?
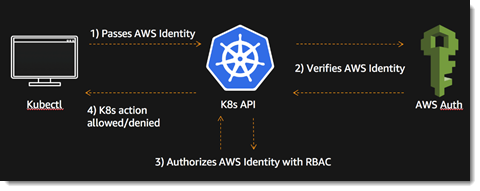
What is Amazon Elastic Kubernetes Service (EKS)?
Top 5 Cybersecurity Predictions for 2020
Micro Lesson: Hosted Collector Overview
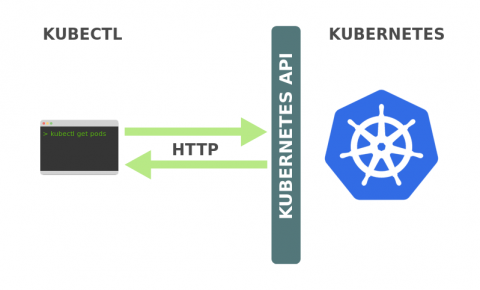
How to View Logs in Kubectl
Kubernetes has become the de-facto solution for container orchestration. While it has, in some ways, simplified the management and deployment of your distributed applications and services, it has also introduced new levels of complexity. When maintaining a Kubernetes cluster, one must be mindful of all the different abstractions in its ecosystem and how the various pieces and layers interact with each other in order to avoid failed deployments, resource exhaustion, and application crashes.
All The Logs For All The Intelligence
If you are reading this, I don’t have to convince you any further of the powerful intelligence we can derive from logs and machine data. If you are anything like the many, many users, customers and prospects we have been talking to over the years, you might, however, have some level of that pesky modern condition commonly known as volume anxiety. The volume here, of course, is the volume of data––there is a lot of it, and it keeps growing.