Operations | Monitoring | ITSM | DevOps | Cloud
Kosli
Maintaining Security with DevOps Compliance
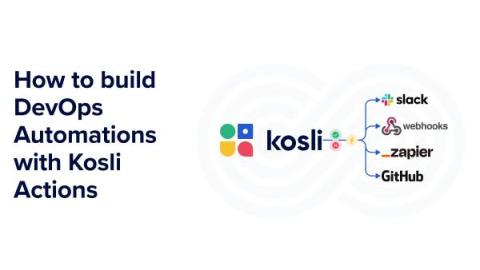
How to build DevOps automations with Kosli Actions
Continuous Compliance Content Hub
The Continuous Compliance content hub is a set of guides for DevOps teams who need to move fast while remaining in compliance for audit and security purposes. We know that the old change management processes for software releases that happened once every 6 months don’t scale for DevOps teams who want to deploy every day. This is where Continuous Compliance comes in.
DevOps Change Management Resources
Understanding ISO27001 Security - and why DevOps teams choose Kosli
Modern software delivery teams find themselves under constant pressure to maintain security and compliance without slowing down the speed of development. This usually means that they have to find a way of using automation to ensure robust governance processes that can adapt to evolving cyber threats and new regulatory requirements.
A Guide to Continuous Security Monitoring Tools for DevOps
DevOps has accelerated the delivery of software, but it has also made it more difficult to stay on top of compliance issues and security threats. When applications, environments and infrastructure are constantly changing it becomes increasingly difficult to maintain a handle on compliance and security. For fast-moving teams, real time security monitoring has become essential for quickly identifying risky changes so they can be remediated before they result in security failure.
The rising trend of Data Breaches and Critical Vulnerabilities in 2023
As the year comes to an end, we are taking a look back on the major data breaches and vulnerabilities that disrupted the security of both small, and large and very important organizations around the world and across all industries. According to a recently published report: As this trend is on the rise, governmental organizations and companies of every size put more emphasis on the security of their systems and networks.
The 5 Best Vanta Alternatives for Security Compliance
Over the last two to three years, we’ve seen increasing demands on all kinds of software companies to comply with security and compliance standards. More and more organizations are looking to benefit by moving their operations to the cloud, but this increases the potential for cybersecurity attacks and breaches. A new type of compliance vendor has emerged to help companies that must comply with the security standards designed to ward off cybersecurity threats.
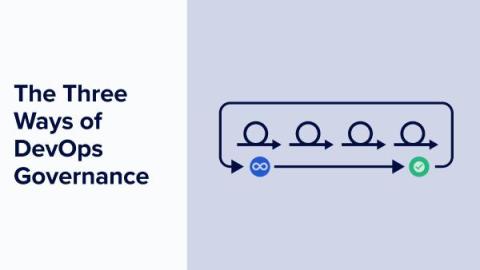
The Three Ways of DevOps Governance
In this blog post, I take a look at modern IT governance by applying the classic “Three Ways” of DevOps principles originally introduced by Gene Kim in his seminal 2012 article. “We assert that the Three Ways describe the values and philosophies that frame the processes, procedures, practices of DevOps, as well as the prescriptive steps.” Here’s a quick reminder of the three ways set out by Gene: For Gene, all DevOps patterns can be derived from these three principles.