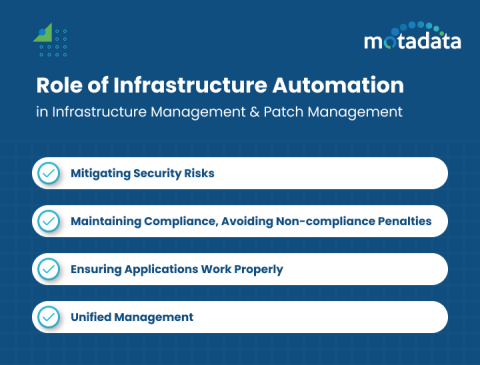
Proactive Patch Management with Infrastructure Automation
Modern enterprises face many challenges, hampering efficiency and innovation amidst tight budgets and safeguarding your brand against escalating cyber threats. Unpatched systems are also prime targets for cybercriminals who aim to access an organization’s sensitive information, intellectual property, and confidential business data. Traditionally, addressing these challenges required many point solutions, creating disjointed management.