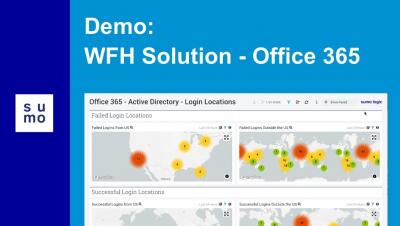
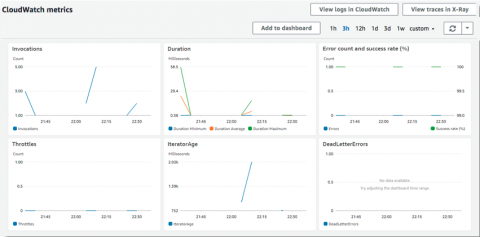
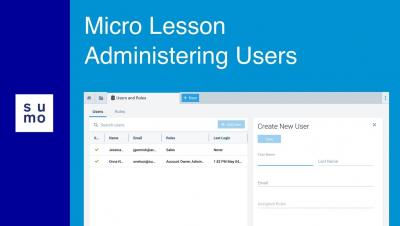
How to build a DevOps pipeline
DevOps is an approach to software development and delivery that emphasizes collaboration between different stakeholders. DevOps also places priority on automation and the integration of different tools in a single, well-oiled pipeline. Ultimately, DevOps boils down to cultural values and goals. When it comes to tooling and processes, there is no one right way to “do” DevOps; a variety of different approaches are possible.