How to Monitor Fastly CDN Logs with Sumo Logic
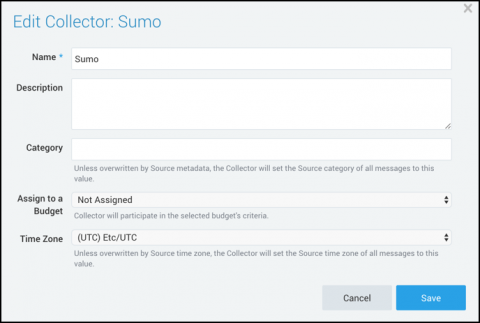
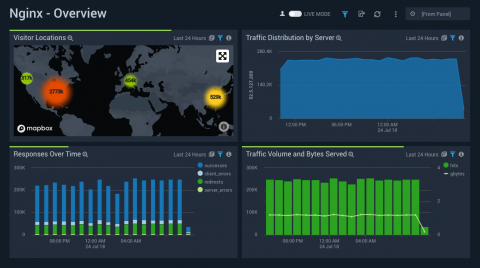
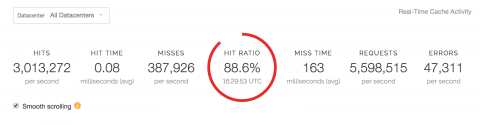
In the last post, we talked about the different ways to monitor Fastly CDN log and why it’s crucial to get a deeper understanding of your log data through a service like Sumo Logic. In the final post of our Fastly CDN blog series, we will discuss how to use Sumo Logic to get the most insights out of your log data — from how to collect Fastly CDN log data to the various Sumo Logic dashboards for Fastly.