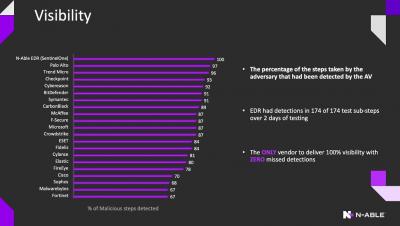
Secure your clients and prevent churn with a canary
Many people are familiar with the stories of coal miners using canaries to detect carbon monoxide and other toxic gases as a warning system for when they should evacuate. Even though cybersecurity is far removed from coal mining, it has an equivalent “canary in the coal mine” that takes the form of indicators of compromise, or IoC for short. So why should an MSP be concerned with looking for IoCs?