Operations | Monitoring | ITSM | DevOps | Cloud
June 2023
How Consolidating Your Tech Stack Drives DEX Outcomes
Every month, it seems that a new “must use” tool hits the market. What ends up happening is IT teams are gifted a hodge-podge of tools — snowballing into unnecessary frustration and increased workloads.
Why Trust Zero Trust Ep. 16
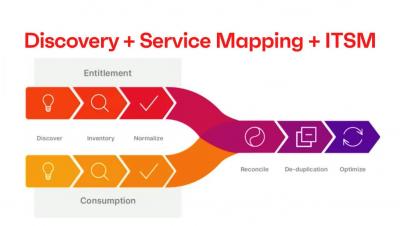
Understanding your IT environment with Discovery, Service Mapping, and, ITSM
The Challenge of Digital Nomads and Work-from-Home Environments
Phishing 2.0: How to Stop Cyberattacks Even Pros Can't Catch
How to Use Generative AI for Knowledge Management
In the blog “How Generative AI Can Benefit Knowledge Management”, we looked at the benefits of AI to knowledge management to enhance the quality, automating the creation of content and enabling more engaging content. In enabling generative AI to become part of the knowledge management framework introduces concerns about accuracy, data bias, privacy and security. Now, it’s time to look at how we can make it work well together...
Employee Performance Management and Remote Work
How Cloud Migration Helps Improve Employee Experience
The old saying goes, “practice what you preach.” When Ivanti started its "Customer Zero" initiative, Bob Grazioli, Chief Information Officer, saw it as a perfect opportunity to test the products and services consumed by customers. For example, during Ivanti’s move to the cloud, Grazioli and the team experienced the same issues that customers would’ve experienced in their migration process. This first-hand experience allowed them to make improvements along the way.
Expand your ITSM: Key learnings for building connected enterprise workflows
How IT Device Discovery Can Identify Your Network's Assets and Vulnerabilities
The security of your organization’s network is paramount to its success. With the ever-changing landscape of cyber threats, it's important to take the necessary steps to ensure that your network is secure and compliant with industry regulations. Ensuring compliance requires you to know what’s on your network. But how can that be done when only 48% of leaders and security professionals say they run their asset discovery program at least once per week?
Tech Confessions - Ancient Artifacts
Work From Home Winning Top-Tier Talent
Tech Confessions - ET, Phone Home | Crazy IT Asset Discovery Stories
The 8 Best Practices for Reducing Your Organization's Attack Surface
Increases in attack surface size lead to increased cybersecurity risk. Thus, logically, decreases in attack surface size lead to decreased cybersecurity risk. While some attack surface management solutions offer remediation capabilities that aid in this effort, remediation is reactive. As with all things related to security and risk management, being proactive is preferred. The good news is that ASM solutions aren't the only weapons security teams have in the attack surface fight.
How Implementing Risk-Based Patch Management Prioritizes Active Exploits
Resistance to change is always present, especially if you think the processes you have in place are efficient and effective. Many organizations feel this way about their software management procedures until they have a security breach or incident and are left wondering where they went wrong. The reality is that most patch management programs are built on assumptions and recommendations, rather than facts about actively exploited vulnerabilities. Risk-based patch management is the answer to this issue.
How Generative AI Can Benefit Your Knowledge Management
There has been growing interest in the capabilities of generative AI since the release of tools like ChatGPT, Google Bard, Amazon Large Language Models and Microsoft Bing. With the hype comes concerns about privacy, PII, security and, even more importantly, accuracy. And rightly so. Organizations are treading cautiously with their acceptance of generative AI tools, despite seeing them as a game changer.
Tech Confessions - Attack of the Toasters | Crazy IT Asset Discovery Stories
Tech Confessions - The Paper Trail | Crazy IT Asset Discovery Stories
There's a Bot for That
AI vs. AI: The Future of Cyber Security Podcast Ep. 14
ITSM's Role in Building a Connected Enterprise: The Perspective of a CIO
With 73% of IT and security professionals reporting an increased workload since hybrid and remote work started, ITSM is a game changer for your organization. By automating workloads and increasing visibility, you’re able to build up the resiliency of your IT operations and proactively resolve problems. But getting started can be hard. That’s why Bob Grazioli, Ivanti’s Chief Information Officer, sat down to share his perspective gathered over more than 25 years in the field.
A CIOs Perspective on ITSM
How ITSM Can Serve as a Single Source of Truth
How to Use Service Tickets to Improve Your Digital Employee Experience
Why IT Asset Discovery Is the Foundation of a Risk-Based Vulnerability Management Program
With over 236,000 total vulnerabilities currently known – and an average 61 new vulnerabilities added every day to the NVD – it’s impossible to remediate every single CVE or threat vector that appears. So, how do everyday organizations handle the continuously growing threats to their organization’s end users, customers and data – especially across an increasingly hybrid and remote Everywhere Workplace?
Three Reasons Endpoint Security Can't Stop With Just Patching
With remote work now commonplace, having a good cyber hygiene program is crucial for organizations who want to survive in today’s threat landscape. This includes promoting a culture of individual cybersecurity awareness and deploying the right security tools, which are both critical to the program’s success. Some of these tools include endpoint patching, endpoint detection and response (EDR) solutions and antivirus software.
How to Start a Knowledge Base: Simple Yet Surefire Approach
Early in my career, I made the jump from defense contractor to customer support agent for an up-and-coming IT Service Management solution provider. Being new to the team and industry, I felt completely out of place. After the initial product training, I was pointed to a lab computer and told to start diagnosing a set of customer issues. I felt completely lost. Over time, with significant amounts of studying and leaning on my peers, I figured things out and eventually became one of the go-to analysts.