Operations | Monitoring | ITSM | DevOps | Cloud
GroundWork
The Role of GroundWork Monitor in Security Monitoring
The GroundWork team has reviewed industry analysis of the recent Kaseya VSA incident, and while details are still being revealed, there are some useful take-aways we want to share. In particular, certain aspects of preparedness and indicators of active compromise can be monitored. We also want to talk a little bit about where GroundWork Monitor fits into security monitoring as a whole.
Mitigating Alarm Fatigue with GroundWork Messenger
GroundWork Monitor Enterprise version 8.2.0 offers enhancements that build on the capabilities we have mentioned in past blogs. While all the dependencies, parent-child, and service and host dependencies are present as before, we have gone through our notification system and revamped it with an eye to making it easier to get the right alerts to the right people, with the right methods.
Home Dashboard
Branding the GroundWork Monitor login page
GroundWork Releases GroundWork Monitor Enterprise 8.2.0
SAN FRANCISCO, May 5, 2021 /PRNewswire/ — GroundWork Open Source, Inc., a leading provider of powerful IT infrastructure monitoring software, today announced the general availability of GroundWork Monitor Enterprise version 8.2.0, its flagship all-inclusive monitoring product.
Application Monitoring with Spring Boot, Prometheus, and GroundWork Monitor
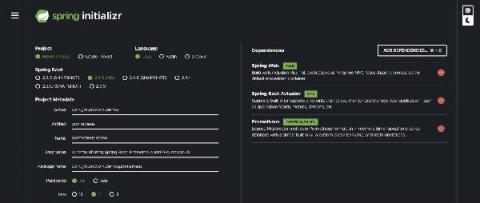
In our previous Blog, we introduced how we use Prometheus and the GroundWork Application Performance Monitoring (APM) connector to instrument a GoLang program to send metrics to GroundWork Monitor Enterprise. In this article, we continue with more Prometheus examples, but this time we demonstrate how to instrument a Java application with Spring Boot for easy monitoring.
Business Service Monitoring (BSM) with GroundWork Monitor
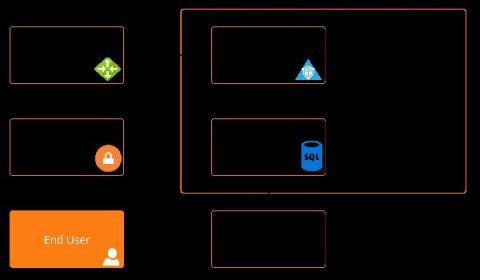
We all want our monitoring systems to alert us when things go wrong. While it’s important to get alerts in the event of a failure or latency problem on something specific such as a SQL database, it’s actually just as important to not receive alerts from too many specific sources in the same alerting channel. If our monitoring system starts to fatigue us, we will ignore alerts until the phone calls and Emails from end users start letting us know a service is impaired or unavailable.
Using Let's Encrypt Free Certs with your Linux Servers
Part 2 of our Blog series on certificates focuses on a practical matter: using the free Let’s Encrypt certificates to secure servers that may not be publicly available, but still need better security than self-signed certs can give you. As we explained in our last blog on this subject, to use HTTPS encryption with certificates, you can choose from a number of options.
7 Ways GroundWork Delivers Bulletproof Infrastructure Monitoring
Lately, security has become top of mind across infrastructure monitoring customers. This is no surprise considering the widespread reports about supply-chain vulnerabilities and embedded compromises rampant in popular network monitoring software. In light of this, we want to underscore how seriously we have always taken our security processes, and how we cultivate a culture based on a foundation of sound security protocols.