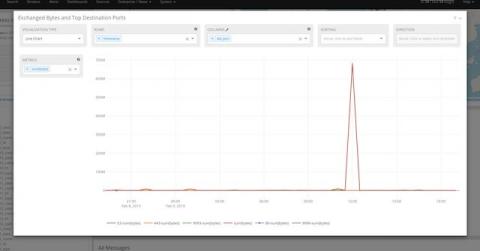
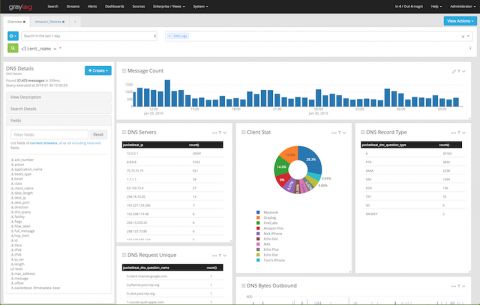
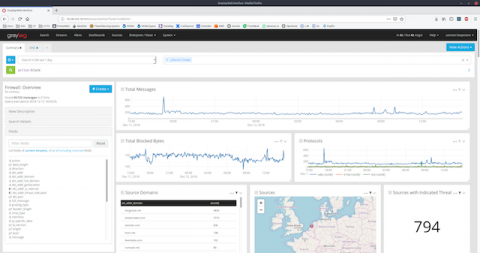
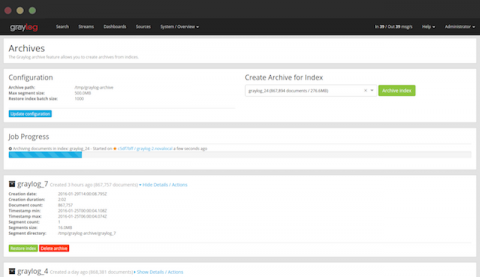
An Introduction to Graylog Aggregation Charts
It’s Sunday afternoon, and you’re having a nice relaxing weekend, sitting down watching your favorite sporting event. While enjoying the game, you get a high alert email on your phone, noting something’s going on and you need to jump into action. What do you do in these high stress times? Every second counts, and everyone is waiting on you to tell them what’s happening.