Importance of System Resource Monitoring on Graylog, Elasticsearch, and MongoDB Servers
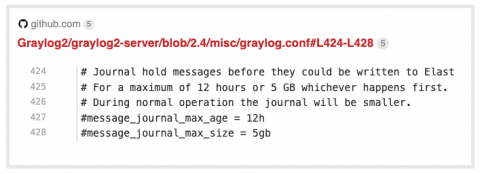
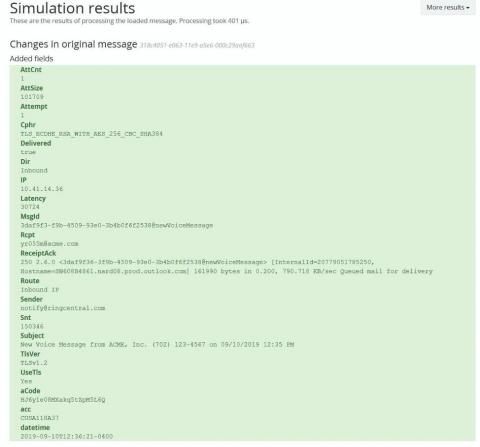
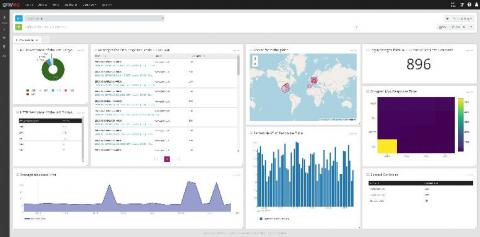
The first thing we tell Graylog users is, “Monitor your disk space.” The core set of metrics discussed below should always be in acceptable parameters and never grow over extended periods without going back to normal levels. This is why it is critical to monitor metrics that come directly from the hosts running your Graylog infrastructure.