Security Hygiene - Why Is It Important?
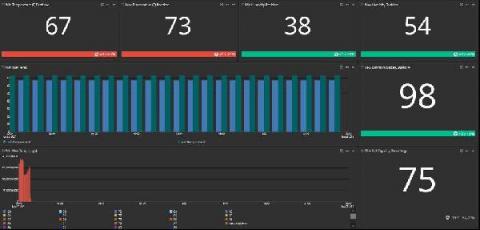
“What happened?” If you’ve never uttered those words, this blog isn’t for you. For those of us in cybersecurity, this pint-sized phrase triggers memories of unforeseen security incidents and long email threads with the CISO. What happened to those security patches? Why didn’t we prevent that intrusion? Organizations tend to lean towards protecting their borders and less towards understanding the importance of overall security hygiene.