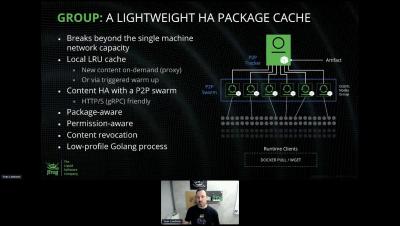
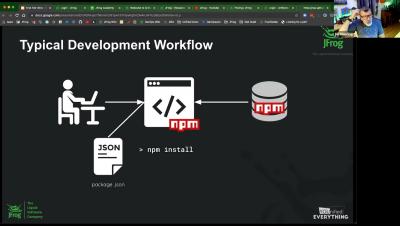
Set Up a Remote Repository in Artifactory To Proxy Iron Bank Images
U.S. Department of Defense (DoD) teams that manage DevSecOps software factories or that use DevSecOps factories to develop, secure and operate mission applications, need a trusted repository management system to store their local artifacts as well as artifacts pulled from Iron Bank, the DoD’s central repository of hardened container images. Artifacts that are stored include VM images, container images, binary executables, archives, documentation and many more package types.