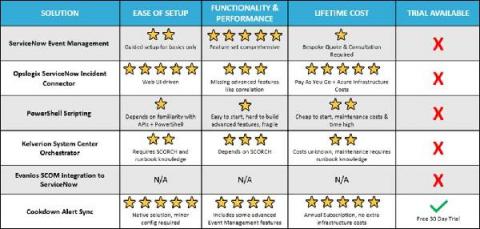
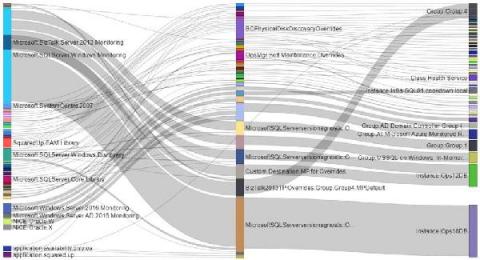
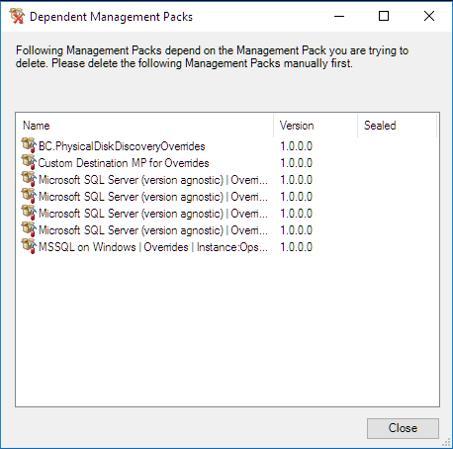
How to get the most from your ITSM monitoring integrations?
Before talking about integration, let’s take a look at your non-automated Service Management processes. There isn’t a right or wrong answer as this varies based on your needs, think through the below questions to get a perspective on how tasks flow within your company today.