Operations | Monitoring | ITSM | DevOps | Cloud
Tigera
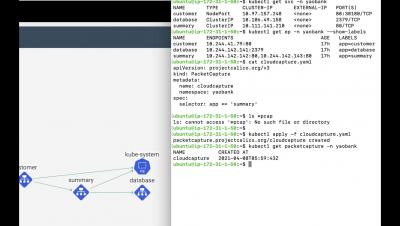
Dynamic Service Graph | Tigera - Long
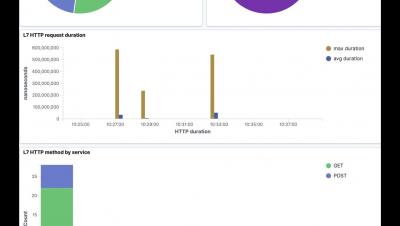
Application Layer Observability | Tigera - Long
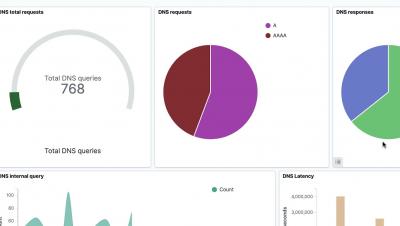
DNS Dashboard | Tigera - Long
Calico Enterprise enables live view of cloud-native apps deployed in Kubernetes
We are happy to announce that the latest release of Calico Enterprise delivers unprecedented levels of Kubernetes observability! Calico Enterprise 3.5 provides full-stack observability across the entire Kubernetes environment, from application layer to networking layer. With this new release, developers, DevOps, SREs, and platform owners get: For more information, see our official press release.
Announcing Calico Enterprise 3.5: New ways to automate, simplify and accelerate Kubernetes adoption and deployment
We are thrilled to announce the availability of Calico Enterprise 3.5, which delivers deep observability across the entire Kubernetes stack, from application to networking layers (L3–L7). This release also includes data plane support for Windows and eBPF, in addition to the standard Linux data plane. These new capabilities are designed to automate, simplify and accelerate Kubernetes adoption and deployment. Here are highlights from the release…
Kubernetes Security and Observability
How Calico Cloud's runtime defense mitigates Kubernetes MITM vulnerability CVE-2020-8554
Since the release of CVE-2020-8554 on GitHub this past December, the vulnerability has received widespread attention from industry media and the cloud security community. This man-in-the-middle (MITM) vulnerability affects Kubernetes pods and underlying hosts, and all Kubernetes versions—including future releases—are vulnerable. Despite this, there is currently no patch for the issue.
TeamTNT: Latest TTPs targeting Kubernetes (Q1-2021)
In April 2020, MalwareHunterTeam found a number of suspicious files in an open directory and posted about them in a series of tweets. Trend Micro later confirmed that these files were part of the first cryptojacking malware by TeamTNT, a cybercrime group that specializes in attacking the cloud—typically using a malicious Docker image—and has proven itself to be both resourceful and creative.
Honeypods: Applying a Traditional Blue Team Technique to Kubernetes
The use of honeypots in an IT network is a well-known technique to detect bad actors within your network and gain insight into what they are doing. By exposing simulated or intentionally vulnerable applications in your network and monitoring for access, they act as a canary to notify the blue team of the intrusion and stall the attacker’s progress from reaching actual sensitive applications and data.