Using Device Telemetry to Answer Questions About Your Network Health
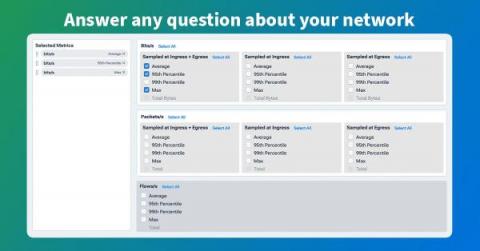
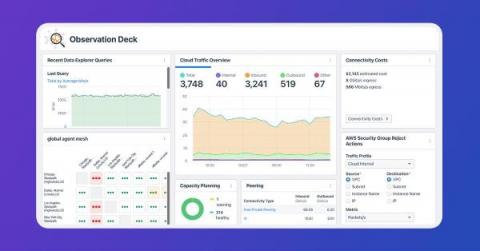
When coupled with a network observability platform, device telemetry provides network engineers and operators critical insight into cost, performance, reliability, and security. Learn how to create actionable results with device telemetry in our new article. For cloud network specialists, the landscape for their observability efforts includes a mix of physical and virtual networking devices.