What Are the Benefits of Monitoring Event Logs?
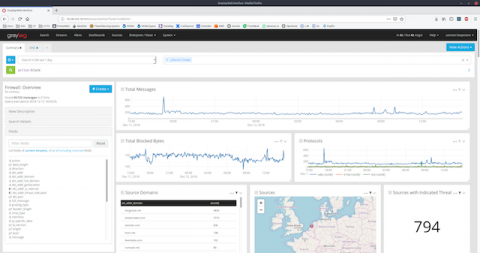
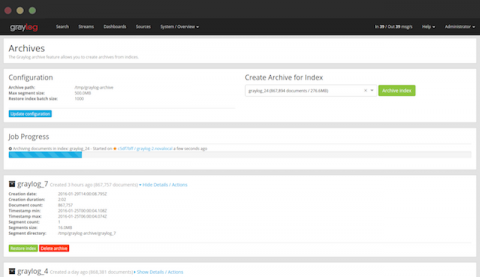
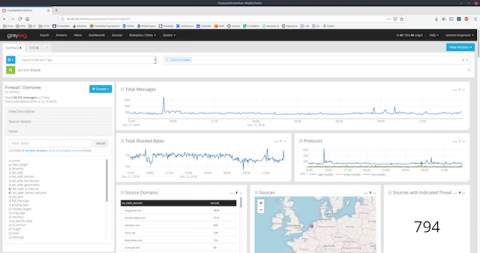
If you maintain a regular practice of keeping log data, you probably have an established way of observing event logs in real time or you do it by using batch processing. There are two ways you can monitor event logs: manually and automatically. By monitoring event logs, you can gain deeper insight into system metrics, localize process bottlenecks, and detect security vulnerabilities. What are some other advantages of event log monitoring, and how can you get the most out of it?