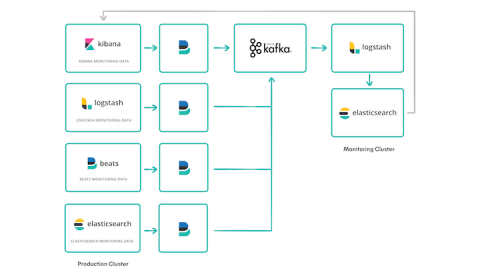
How to create maintainable and reusable Logstash pipelines
Logstash is an open source data processing pipeline that ingests events from one or more inputs, transforms them, and then sends each event to one or more outputs. Some Logstash implementations may have many lines of code and may process events from multiple input sources. In order to make such implementations more maintainable, I will show how to increase code reusability by creating pipelines from modular components.