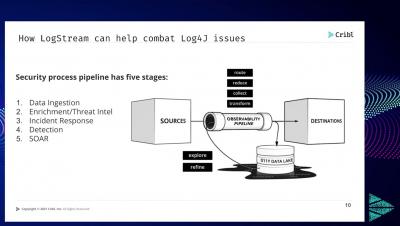
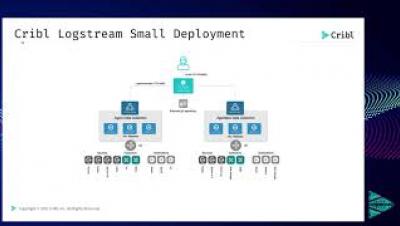
Momma Said Grok You Out: Use LogStream to Streamline Searches, Aid in Reformatting Data and Parsing
It is commonly believed that once data is collected and ingested into a system of analysis, the most difficult part of obtaining the data is complete. However, in many cases, this is just the first step for the infrastructure and security operations teams expected to derive insights.