Software Development Optimization - Sumo Logic
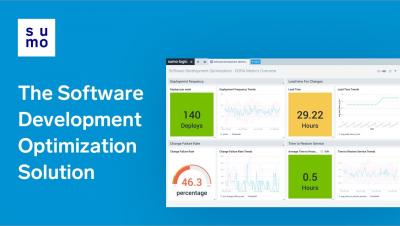
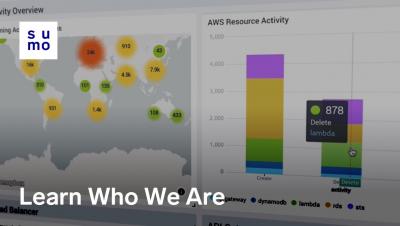
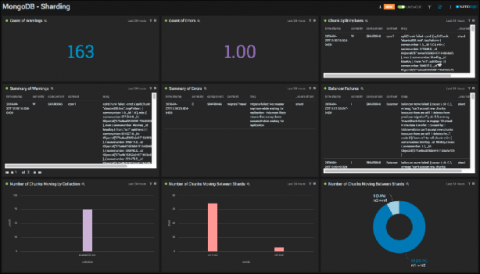
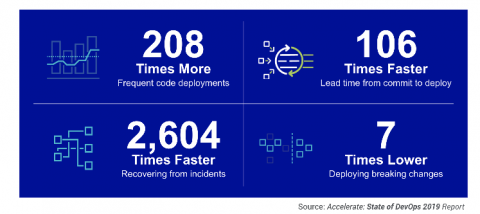
Increase release velocity, improve reliability and comprehensively monitor CI/CD pipelines with industry leading metrics and actionable insights generated automatically from Jira, GitHub, Jenkins, PagerDuty, Bitbucket, Opsgenie, and more.