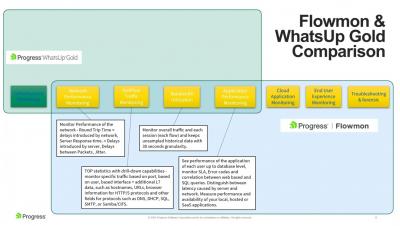
Operations | Monitoring | ITSM | DevOps | Cloud
March 2022
WhatsUp Gold Lesson: How Do I Configure a Device to Monitor My Voice over IP (VoIP) SLA?
WhatsUp Gold provides specialized Voice over Internet Protocol (VoIP) Service Level Agreement (SLA) monitoring necessary for tracking Quality of Service (QoS) and SLA metrics for your network of deployed VoIP devices (telephones, conference room devices and more). After you discover and configure devices for VoIP monitoring, you can view results and graphs on the WhatsUp Gold Custom Performance Monitors dashboard.
Advanced Network Traffic Analysis and Enhanced Security in the New, Easier-to-Use-Than-Ever WhatsUp Gold 2022.0
Part of our job here at Progress is to not only look at the challenges our customers are currently facing, but also to look at the technology landscape in general and consider the challenges they’re going to be facing. We don’t have a crystal ball, of course, but there are a plenty of trends that are obvious to even the most casual observer. Security has always been important, but the last year has made it clear exactly how important it is for every organization with a network.
Financial Services Network Challenges: Compliance, Security and Availability Top Concerns
Financial services firms face three key network issues: maintaining compliance with an array of regulations, keeping a growing horde of financial data hungry hackers at bay, and earning the trust of users with an always-on responsive network. Financial data is so valuable, cybercriminals make getting it a top priority. And financial services networks are so interconnected and complex, there are all sorts of ways hackers can try to break in. The security threat to finance is more than bad.
Keeping Federal and Local Government Networks Safe Through Monitoring
It is always big news when governmental organizations are attacked. And they are attacked frequently. Hackers love headlines, which is one reason to go after high profile government targets. But the real reason hackers love governmental organizations is because that’s where the juicy data is. Even small governmental organizations hold confidential and classified information—exactly the secrets state-sponsored groups and other cybercriminals drool over.
Supporting, Extending, and Protecting Virtual Environments
Get to Know WhatsUp Gold Free Edition
We sympathize with the IT teams that keep their networks running – we really do. We understand it’s a thankless job where they’re ignored if everything’s working and blamed when everything’s not. That’s why we’ve tried to make our network infrastructure and application experience (AX) products as simple and intuitive as possible.
What Healthcare Companies Need from Network Management and Network Monitoring
IT pros in the healthcare industry have one of the toughest jobs imaginable. Herculean task number one is protecting patient data, with failure to do so bringing hefty HIPAA fines and more than a little bad press. Gargantuan task number two is stopping breaches (and then doing forensics if one busts through). Failing either of these is not exactly a confidence booster. Don’t forget, almost all hacks and breaches either attack the network itself or go across it to reach their target.