Operations | Monitoring | ITSM | DevOps | Cloud
Tigera
Enforcing Enterprise Security Controls in Kubernetes using Calico Enterprise
Hybrid cloud infrastructures run critical business resources and are subject to some of the strictest network security controls. Irrespective of the industry and resource types, these controls broadly fall into three categories. Workloads (pods) running on Kubernetes are ephemeral in nature, and IP-based controls are no longer effective. The challenge is to enforce the organizational security controls on the workloads and Kubernetes nodes themselves.
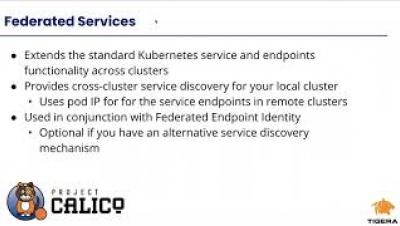
Calico Enterprise Multi Cluster Management - Federated Identity and Services
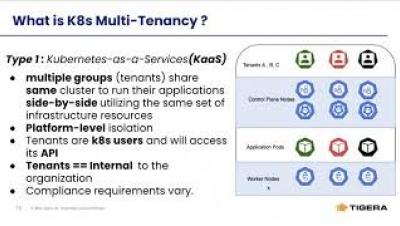
How Calico Enterprise Enables Your Kubernetes Multi-Tenancy
Enabling Microsegmentation with Calico Enterprise
Microsegmentation is a security technique that is used to isolate workloads from one another. Microsegmentation limits the blast radius of a data breach by making network security more granular. Should a breach occur, the damage is confined to the affected segment. Application workloads have evolved over time – starting from bare metal, to a mix of on-prem and cloud virtual machines and containers.
Enterprise Security Controls for Kubernetes
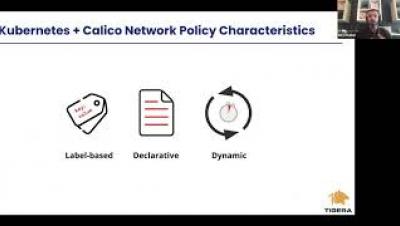
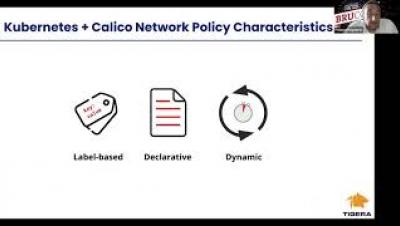
Calico and K8s Network Policies - An Overview and Comparison
Calico Enterprise Multi Cluster Management
Egress access control for Kubernetes
Announcing the Tigera - Nutanix Partnership
Today we are pleased to announce our partnership with Nutanix, creators of the industry’s most popular hyper-converged infrastructure (HCI) technology. HCI combines datacenter hardware using locally-attached storage resources with intelligent software to create flexible building blocks that replace legacy infrastructure consisting of separate servers, storage networks, and storage arrays.