Enhancing AWS security with Graylog centralized logging
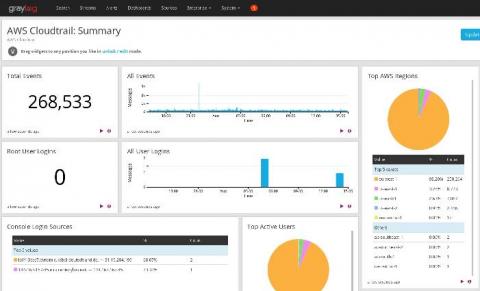
AWS is a popular destination for IaaS that offers quickly saleable resources to meet even the largest customer demands. Cloud scalability like this can generate a large amount of logs you need to monitor to keep up with your cybersecurity goals. Getting those logs into a SIEM or centralized log management platform such as Graylog is key to have proactive monitoring and alerting.