Sponsored Post
How to Threat Hunt in Amazon Security Lake
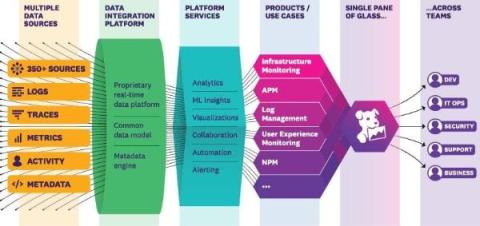
Establishing a proactive security posture involves a data-driven approach to threat detection, investigation, and response. In the past, this was challenging because there wasn't a centralized way to collect and analyze security data across sources, but with Amazon Security Lake it is much simpler. Whether you're a security company improving and refining your threat intelligence for customers, or you're investigating security threats within your own environment, there are a few important things you need to know. This blog will cover the tools, frameworks and data types you'll need to threat hunt in Amazon Security Lake.