Operations | Monitoring | ITSM | DevOps | Cloud
January 2021
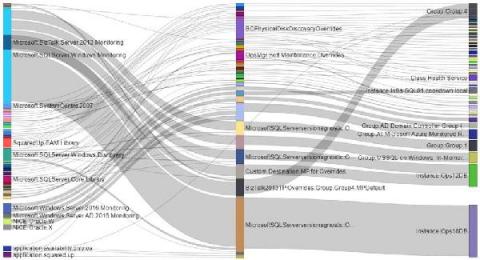
Download PowerBI Diagram for visualizing overrides using Sankey
Did you catch our recent webinar on how PowerBI makes it possible to visualize override sprawl in SCOM with Sankey Diagrams and want to give our Sankey diagrams a go yourself? You are in the right place. Before you dive in, take a look at our blog explaining the “why” to using Sankey PowerBI diagrams to see your overrides, and how to take action based on what you see here.
Overcome security challenges with ServiceNow CMDB population
Networks always start off small and simple, but over time they can become increasingly complex. You start with a small network consisting of a simple Virtual Local Area Network (VLAN) with broad connectivity. However, once your security team get involved and add DMZs, routers, firewalls, etc you will find it hard to keep track of the intricate web you have created to support your business network.
Top integration tools to populate your CMDB
A Configuration Management Database (CMDB) is critical in supporting services such as Incidents and Change & Asset Management. Most companies dream of having a beautifully populated CMDB, but struggle with how to make this a reality as the process can be quite daunting! But never fear there are loads of tools you can buy to do just this! Typically, there are three types of solutions designed to populate your CMDB, these are either agent-based, scanner, or integration style tools.
Bringing override sprawl under control with PowerBI
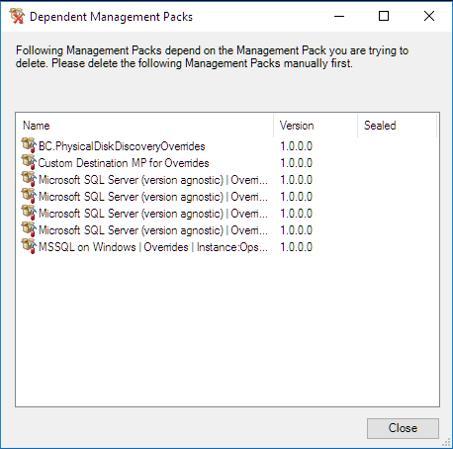
Picture this scenario - the final SQL 2008 server is decommissioned and all replacement SQL servers are monitored using the SQL version agnostic MP - finally! But, before cracking open the bubbly, you will want to pull out the MPs relating to SQL 2008 from SCOM. Easy…? Just delete them from the console… wrong!