Microsoft Releases Out-of-band Updates to Address Critical Windows Server Domain Controller Issue
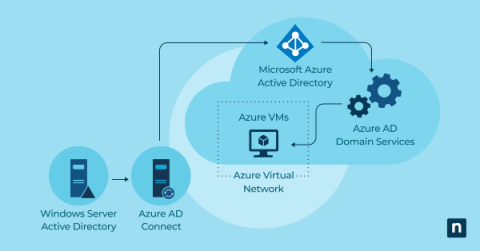
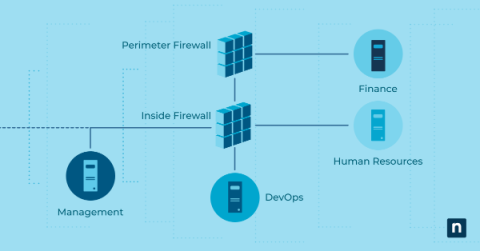
In a recent development that has sent ripples across the IT landscape, Microsoft has identified a critical issue plaguing Windows Server Domain Controllers (DCs). This issue, originating from a memory leak within the Local Security Authority Subsystem Service (LSASS), has emerged as a significant concern for organizations relying on both on-premises and cloud-based Active Directory domain controllers to process Kerberos authentication requests.