The Top Five Benefits of SaaS IT Management Solutions
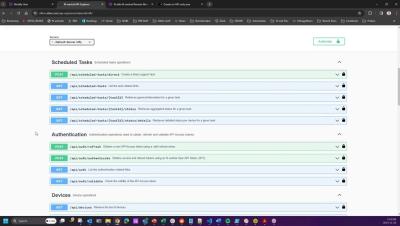
Businesses today face a myriad of challenges. Traditional on-premises IT solutions, which were once the cornerstone of the industry, are now progressively falling behind, outshined by the efficiency, security, and adaptability that SaaS-based solutions bring to the table.