Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
Eliminating Misunderstandings Between InfoSec and IT Operations
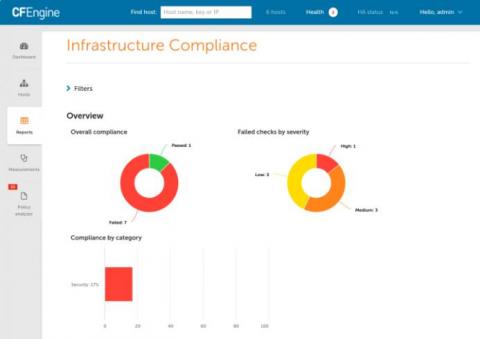
CFEngine 3.16 - Compliance
Today we announce the newest additions to CFEngine. CFEngine 3.16 brings several improvements, bug fixes, and new features. The theme for this release has been compliance, and it notably includes a new category of reports for proving compliance to regulation and other compliance frameworks in high level, easy to read reports. If you are interested to learn more about CFEngine, schedule training, or hear about pricing options, feel free to reach out to us!
DevOps - The Path to Continuous Compliance and Better Security
How to choose the right compliance management software for your business
While keeping data safe from modern cyberthreats is difficult enough, you also have to keep in mind compliance with common regulations, i.e., ensuring your company’s compliance to SOX, which deals with transparency in disclosures from public companies. Nowadays, it’s not enough for businesses to rely on dismissive financial documents that satisfy the intermittent audit; you need to level up your game, and create detailed day-to-day records of activities.
Enforcing CIS compliance with Puppet
Passing an audit is hard — whether you’re in retail, healthcare, finance, or honestly, any industry that values security. Most organizations these days are faced with regulatory standards that must be enforced, which bring both technical and business challenges that are difficult to overcome.
FIPS 140-2: Stay compliant and secure with Canonical
FIPS 140-2 is a set of publicly announced cryptographic standards developed by the National Institute of Standards and Technology. It is an essential part of FEDRamp requirements for many governmental agencies in the US and Canada, as well as their business partners from all around the world. Furthermore, as a well established and verified security standard, an increasing number of large companies and financial institutions are asking for FIPS compliance.
Patient Record Retention: Tips for Compliance and Protection
With the implementation of electronic health records (EHRs) into practices, patient experience has improved, among other advancements at the point of care. These include better access to patient records and highly efficient care delivery. While these are some significant benefits, some practices experience certain drawbacks too, such as temporary slowdown of processes during EHR transition and high ongoing maintenance costs. One of the most pressing issues include patient record retention.
Compliance Made Easy with JFrog Xray
As compliance managers, we often find ourselves in a struggle. Our responsibility is to uphold compliance standards but in order to achieve this, we need to “sell” the concept to the relevant stakeholders, inter alia the business teams and R&D. We’re put in the position of justifying required changes and processes and are thus mistakenly perceived as business “stoppers” and not enablers.
Audit Log: Feature Guide for Security and Compliance
In computing, an audit log is a record of an event. An event is any significant action that impacts the hardware or software of a computer – anything from a mouse click to a program error. Besides documenting which resources were accessed and what for, an audit file system will also include the source and destination addresses, the timestamp, and the user ID information.