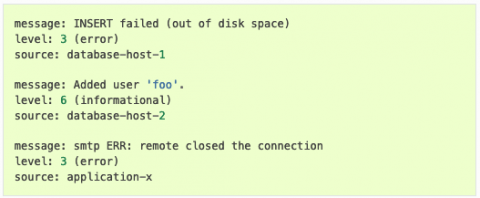
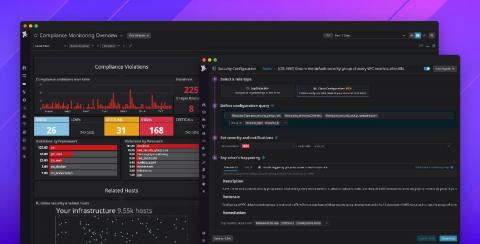
SOC 2 compliance for containers and Kubernetes security
This article contains useful tips to implement SOC 2 compliance for containers and Kubernetes. The Service Organization Controls (SOC) reports are the primary way that service organizations provide evidence of how effective their controls are for finance (SOC 1) or securing customer data (SOC 2, SOC 3). These reports are issued by the American Institute of Certified Public Accountants (AICPA).