Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Restricting CFEngine to one CPU core using Systemd
In some performance critical situations, it makes sense to limit management software to a single CPU (core). We can do this using systemd and cgroups. CFEngine already provides systemd units on relevant platforms, we just need to tweak them. I’m using CFEngine Enterprise 3.12 on CentOS 7, but the steps should be very similar on other platforms/versions.
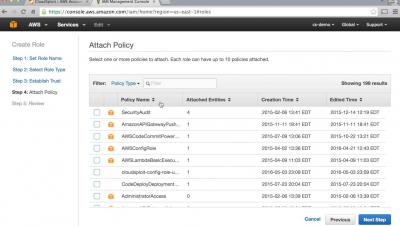
Creating a Cross Account IAM Role in AWS for CloudSploit
The Connected Home - How Secure Are All These Gadgets?
Connected or smart homes are becoming more commonplace as people use computer networks to control different aspects of their in-house technology. But how secure are these networks?
Simplifying security auditing, Part 3: Keeping insider threats in check
Insider threats are on the rise. In fact, both administrators and average employees are among the biggest security threats in an organization. When it comes to security auditing, there are two areas you need to focus on: Active Directory changes and individual user activity, particularly administrator activity.
Security Best Practices: Lessons Learned at a High-Growth Startup
Over the past few years, cybersecurity has become an integral part of operating an organization. Yet there are still plenty of small businesses that know very little about security or where to start. Most think they can get away without paying too much attention to security since they’re not a big target and they don’t have much that is worth stealing.
Completing IT Security With Critical Alerting
Businesses and organizations shouldn’t simply rely on monitoring tools for security management. Such tools don’t provide redundancies, time-stamped audit trails and other elements needed for incident resolution. Also, security threats are rampant and tend to go unchecked even with the most reliable monitoring service. That’s why companies require critical alerting to become aware of security incidents and immediately solve them for business continuity.
Simplifying security auditing, Part 2: Auditing systems that store sensitive data
In part 1, we looked at an overview of auditing servers. In this blog, we’ll discuss which events you need to audit in your databases and file servers where sensitive data is stored. New data protection regulations and large-scale global attacks have made this more important than ever before. The main goal is to not only ensure that the accesses and modifications to sensitive data in your network are authorized, but also that file and column integrity are maintained.
Simplifying security auditing, Part 1: Regularly reviewing server activity
Everyone knows about the importance of log management in IT security. Yet, organizations struggle with implementing effective log management techniques in their networks. This blog series aims to revisit the fundamentals of log management and discuss the different security events you need to keep track of in each of the different systems in your environment.