- November 2019 (1)
- October 2019 (1)
- August 2019 (1)
- June 2019 (1)
- February 2019 (1)
- December 2018 (1)
- August 2018 (1)
- May 2018 (1)
- April 2018 (1)
- January 2018 (1)
- December 2017 (1)
- November 2017 (3)
- July 2017 (3)
Automated AWS Security and Configuration Monitoring.
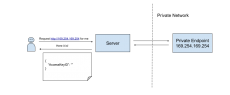
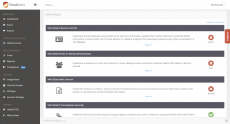
CloudSploit is an open source security and configuration scanner that can detect hundreds of threats in your AWS account. With each scan, CloudSploit securely connects to an AWS account through the AWS APIs, checking for potential risks and misconfigurations that could compromise the account. Don't let a single misstep compromise your entire infrastructure.
CloudSploit helps devops, management, security, and legal teams maintain a secure and compliant cloud infrastructure environment by validating hundreds of settings across every AWS region.
AWS provides the tools for security. CloudSploit helps you use them correctly.
- Free Your Developers: Auditing AWS account security can consume hours of developer time each week. CloudSploit automates the detection of risks on a continuous basis.
- Make Compliance a Priority: The scan reports generated by CloudSploit can be used to quickly assess risk, plan for remediation, and audit changes over time. Legal's happy. You're happy.
- Protect Your Customers: Misconfigurations put your customers' data and your business at risk. Look what happened to CodeSpaces. CloudSploit detects these risks before they are exploited.
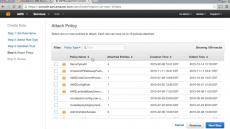
Misconfigurations, open security groups, permissive IAM roles. Scan for these threats and more for free.