Ransomware: How to Combat a Growing Threat to Your Organization
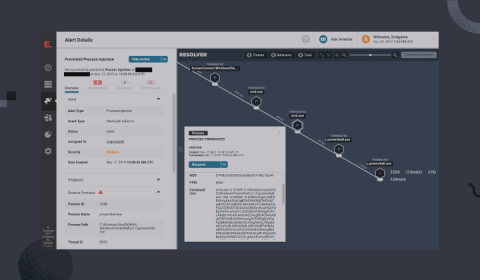
Ransomware is a serious threat to institutions of all kinds, resulting in mounting costs for organizations that must literally pay ransom to regain access to their essential systems. A ransomware attack takes place when a cybercriminal denies an organization access to the data it needs to conduct business, usually by encrypting the data with a secret key. The attacker then offers to reveal the encryption key in exchange for a payment. The payment can vary in amount or kind.