Vaccinating Against the Ransomware Pandemic
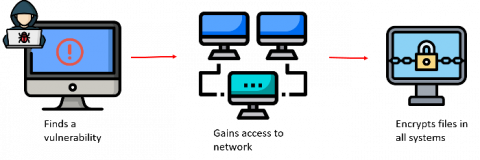
Just as our physical world has suffered from a devastating health pandemic, over the last 3 years the digital world has been suffering a ransomware pandemic that grew 7 times in 2020 compared to the same time in 2019. While we have vaccines for our health crisis what are our options to help protect us against this digital threat?