Monitoring the IBM Power Ecosystem using Microsoft Azure
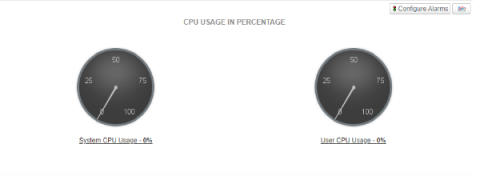
In today’s interconnected and hybrid cloud environments, effective system monitoring is crucial for maintaining performance, reliability, and security. This technical presentation explores how Microsoft Azure enables comprehensive monitoring of the IBM Power ecosystem, explicitly focusing on AIX, Linux on Power, and Linux on Z Series operating systems. Further, active monitoring of HMC and VIOS is considered.