Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
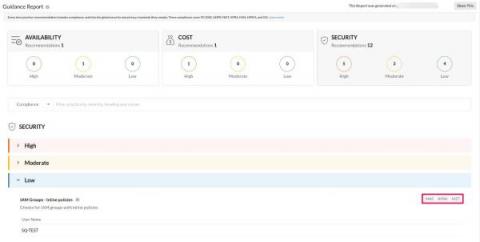
Top 7 compliance checks that you shouldn't miss in AWS monitoring
AWS Monitoring-Guidance report compliance checks As a business owner, you may experience lapses in the compliance and security checks in your AWS environment. With Site24x7 AWS guidance reports, businesses can ensure their deployments adhere to standards in cost, performance, and the security of their AWS environment and make informed decisions about how to optimize their cloud infrastructure.
Blancco's Newly Transformed Global Partner Program Foundational to Doubling its Enterprise Business by 2025
Docker container security: demystifying FIPS-enabled containers with Ubuntu Pro
In today’s rapidly changing digital environment, the significance of robust Docker container security measures cannot be overstated. Even the containerised layer is subject to compliance standards, which raise security concerns and compliance requirements. Docker container security measures entail safeguarding our lightweight, appliance-type containers –each encapsulating code and its dependencies– from threats and vulnerabilities.
The Importance of Compliance for Small and Medium-Size Businesses: What You Need to Know
Navigating compliance requirements can be complex because there are so many of them, and there is a good chance that at least one set of standards applies to you. Standards can be for specific sectors, like The Health Insurance Portability and Accountability Act (HIPAA) for healthcare, or may apply more generally to organizations across industries, like the General Data Protection Regulation (GDPR).
How to Perform an ISO 27001 Audit
The Definitive ISO 27001 Checklist to Implement the Standard [+Free Download]
What is SOC Compliance? Basic Overview for Businesses
IBM reports that the global average total cost of a data breach in 2022 was $4.35 million. Data breaches are rising each year, with an ever-increasing cost, so it’s absolutely essential to be prepared and proactive in your data protection strategy. When clients provide personal or business data to an MSP, they expect the provider to have proper policies and procedures in place to protect that data.