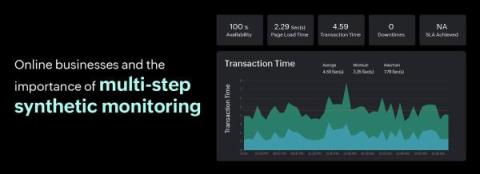
Top 3 reasons why you need to use Site24x7's thread dump analyzer tool
Imagine having x-ray vision for your application and seeing exactly what's happening under the hood in real time. That's what thread dumps do for your application—they are a vital component of application performance monitoring (APM) and give you a super-powered peek into its inner workings, helping you spot issues and fix them faster than you can imagine.