2023's Top Vulnerabilities and the Power of Patch Management
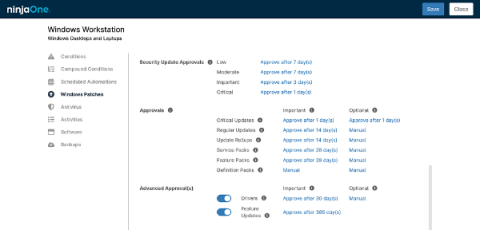
The cybersecurity landscape in 2023 was increasingly complex, marked by sophisticated cyber threats such as ransomware and cyber espionage. Over half of the high-risk vulnerabilities were exploited by threat actors, with ransomware payouts averaging a significant $1,542,333, up from $812,380 in 2022. Phishing attacks dominated, accounting for over 80% of incidents, and 57% of organizations experienced frequent phishing attempts. Additionally, 4,000 ransomware attacks occurred daily since 2016.