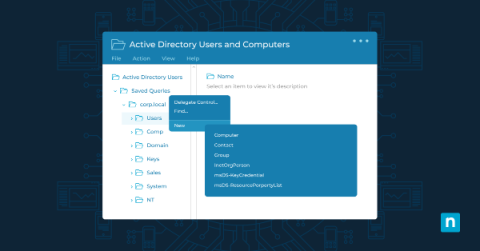
How to Install Active Directory (AD) Users and Computers (ADUC)
Active Directory Users and Computers (ADUC) is a management tool that provides a graphical user interface for managing and organizing the elements of a Windows Active Directory (AD) domain. Key functions include user, group, organizational unit, and computer management, as well as control of security and permissions and trust relationships between domains. ADUC provides system administrators with a centralized interface, simplifying complex tasks and enhancing the security of Windows environments.