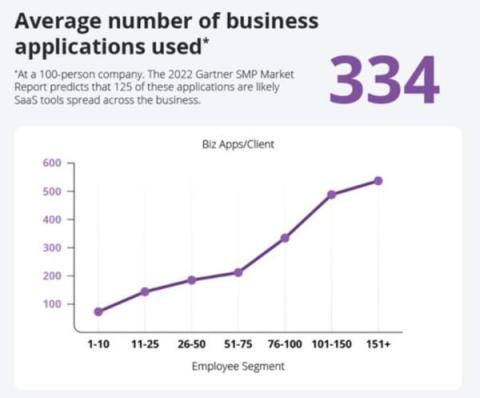
SLA Management Best Practices for IT Services
The cornerstone of every successful relationship—business or otherwise—is a clear, mutual set of expectations. In IT, this plays out in the form of service level agreements (SLAs). But really, SLAs are only the first step in the journey to a happy customer relationship. The real key to maintaining happy customers over the long term is SLA management. Knowing how important SLAs are raises several questions: How do you create one, what should it contain, and how do you manage them?