Time Zones: A Logger's Worst Nightmare
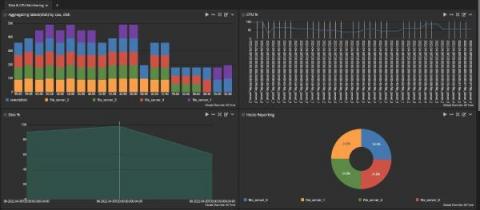
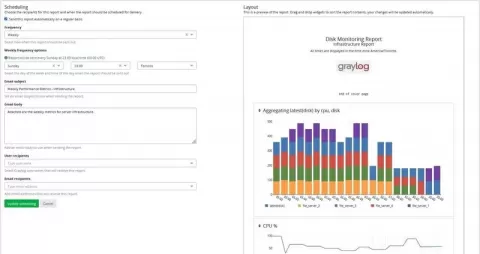
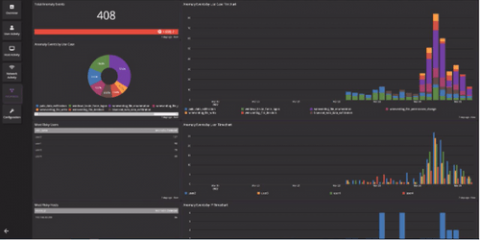
When working with log messages, it’s critical that the timestamp of the log message is accurate. Incorrect timestamps can cause problems when trying to find log messages at a specific date/time or may cause alerts to not function properly. A common cause of incorrect timestamps for log messages is a mismatch of time zones between the log source (device sending the log) and log destination (device receiving the log, such as Graylog).