Elevate Your Security with 8 Network Segmentation Best Practices
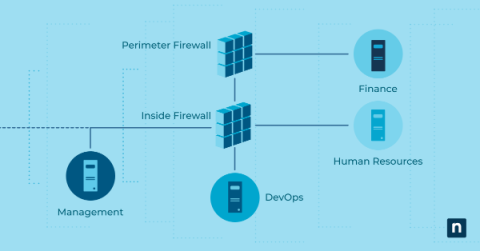
There are many moving parts to a zero trust strategy, and network segmentation cybersecurity is an important piece of the puzzle. Network segmentation involves dividing a network into smaller, isolated segments to minimize the potential damage caused by unauthorized access or attacks. In this article, we will explore the role of network segmentation in security, the key principles behind it, and eight network segmentation best practices to implement it effectively.