Operations | Monitoring | ITSM | DevOps | Cloud
Cyberattacks
Configure a policy to detect and block attacks and exploits
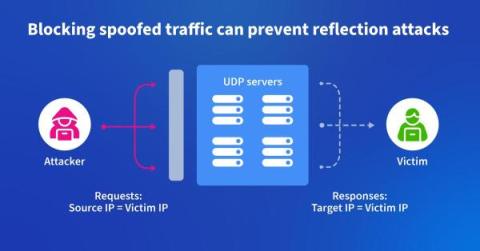
Using Kentik to Fight DDoS at the Source
In this blog post, we describe how one backbone service provider uses Kentik to identify and root out spoofed traffic used to launch DDoS attacks. It’s a “moral responsibility,” says their chief architect.
Detecting and Preventing Brute Force Attacks with PowerShell
While cyber threats are certainly continuously evolving, the fact is most intrusions still rely on basic, tried-and-true techniques. Who needs to burn a zero-day if guessing commonly used passwords or exploiting passwords used across multiple accounts can give you easy access? Brute force attacks continue to be an incredibly common threat that organizations face.
The Impact of Cyber Security on Disaster Recovery and Continuity Planning
G2's Most Recommended WAF & DDoS Protection
In case you missed it, HAProxy Technologies recently put out a press release about our stunning leadership position in G2’s Summer 2023 Grid® Reports for load balancing. We’re incredibly proud of these results, which are a direct result of the hard work and dedication of HAProxy’s community developers and our enterprise product and support teams. Looking at the Momentum Grid® Report for Load Balancing, the gap between HAProxy and the rest is impossible to ignore.
Common API Vulnerabilities and How to Secure Them
Top 10 Security Tips for a New Real Estate Website
How Kentik reduces the likelihood of a full-blown cyber-attack before it happens
Organizations are under constant attack, and it’s critical to reduce the time it takes to detect attacks to minimize their cost. This first article in our new security series dives deep into how Kentik helps customers before, during, and after a cyber attack.