Understanding RBVM & Application Security Orchestration & Correlation
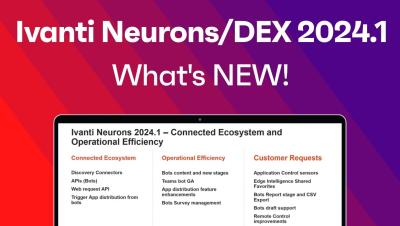
The video introduces Risk-based Vulnerability Management (RBVM) and Application Security Orchestration and Correlation (ASOC), tools that integrate third-party data into a SaaS platform for threat analysis and risk scoring. It highlights recent improvements, new export capabilities, UX updates, and custom attributes for data uploads. It also explores the vulnerability response feature, which integrates RBVM and ASOC with ITSM for automatic ticket creation and security incident syncing, and the RBVM and patch integration for CVE analysis and patch management.#Risk-based Vulnerability Management, #Application Security Orchestration and Correlation, #ITSM integration, #patch management, #CVE analysis.