How IT Managers and MSPs can drive transformation with Remote Monitoring and Management (RMM)
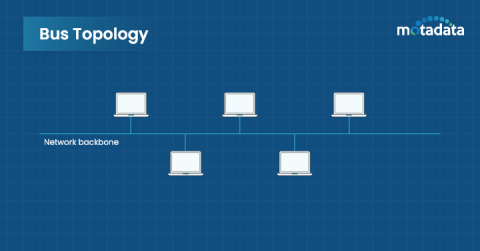
Managing multiple vendors in an IT ecosystem can be daunting and fraught with risks. From the complexities of contract negotiations and renewals to the compliance challenges, the process is often time-consuming. In such a scenario, RMM Tools can help, a unified, scalable solution that can streamline various aspects of IT and network infrastructure, reducing the administrative burden and enhancing operational efficiency.